Following the previous article Home Streaming Solution - Jellyfin: I have a unique usage method - zfsjlll's private space, after tinkering with streaming media, my WinNAS has been moved to my hometown for long-term placement. Due to changes in the network environment and the service of the ISP, the home broadband has changed from gigabit to 300Mbps, and the dynamic public IPv4 is gone, so I need to redesign the remote access plan.
(You can check the previous plan at Cloudflare CDN Open Port - zfsjlll's private space)
1. Analysis of Demand Scenarios and Pain Points#
- Typical dilemmas of remote access to home NAS:
- Stability issues with dynamic public IP
- The awkwardness of ISP blocking ports 80/443
- Security risks of HTTP plaintext transmission
Simulated user login
Request URL: http://vulnerable-site.com/login
Form fields: username=admin&password=123456
Wireshark captures HTTP packets, leading to privacy leaks
POST /login HTTP/1.1
Host: vulnerable-site.com
Content-Type: application/x-www-form-urlencoded
Content-Length: 28
username=admin&password=123456
2. Overview of Technical Solutions#
[User Browser] --HTTPS(443)--> [CDN Node] --HTTP(Custom Port)--> [Reverse Proxy Server] --> [WinNAS Service]
- Key technical components:
- The CDN is of course chosen to be Cloudflare, which is very friendly to individual webmasters. It does have some technical thresholds, but it's all free, what more could you want? (laughs)
- The reverse proxy does not use common Nginx/Caddy; recently, Lucky has become particularly popular in the NAS community, capable of achieving: soft and hard routing public network magic, ipv6/ipv4 port forwarding, reverse proxy, DDNS, WOL, ipv4 stun internal penetration, cron, acme, Alibaba Cloud disk, ftp, webdav, filebrowser. The functionality is completely sufficient, and it's very user-friendly for beginners, with a graphical interface. Official website: Lucky
3. Practical Deployment Steps#
3.1 Basic Network Architecture Setup
Specific deployment tutorials can be searched online; here we only discuss the essentials, all advanced techniques.
- Dynamic domain name resolution plan (Silent deployment of Lucky tool on Windows services)
- Reverse proxy configuration (still using Lucky)
- In addition to DDNS and reverse proxy modules, there are many practical features to explore, such as port forwarding, remote wake-up, network storage (implementation of servers for protocols like WebDav, FTP, etc., I have already deployed Alist, which is not needed for now), etc. (Similar to soft routing ALL IN ONE? I have not deployed soft routing, please correct me if I'm wrong)
3.2 CDN Layer Security Transformation
- Port hiding technique: Achieve URL redirection through CDN's "Page Rules" (using Cloudflare as an example):
- Create a rule to implement:
*.yourdomain.com/*→ Forward tohttp://nas.yourdomain.com:yourport$1
- Create a rule to implement:
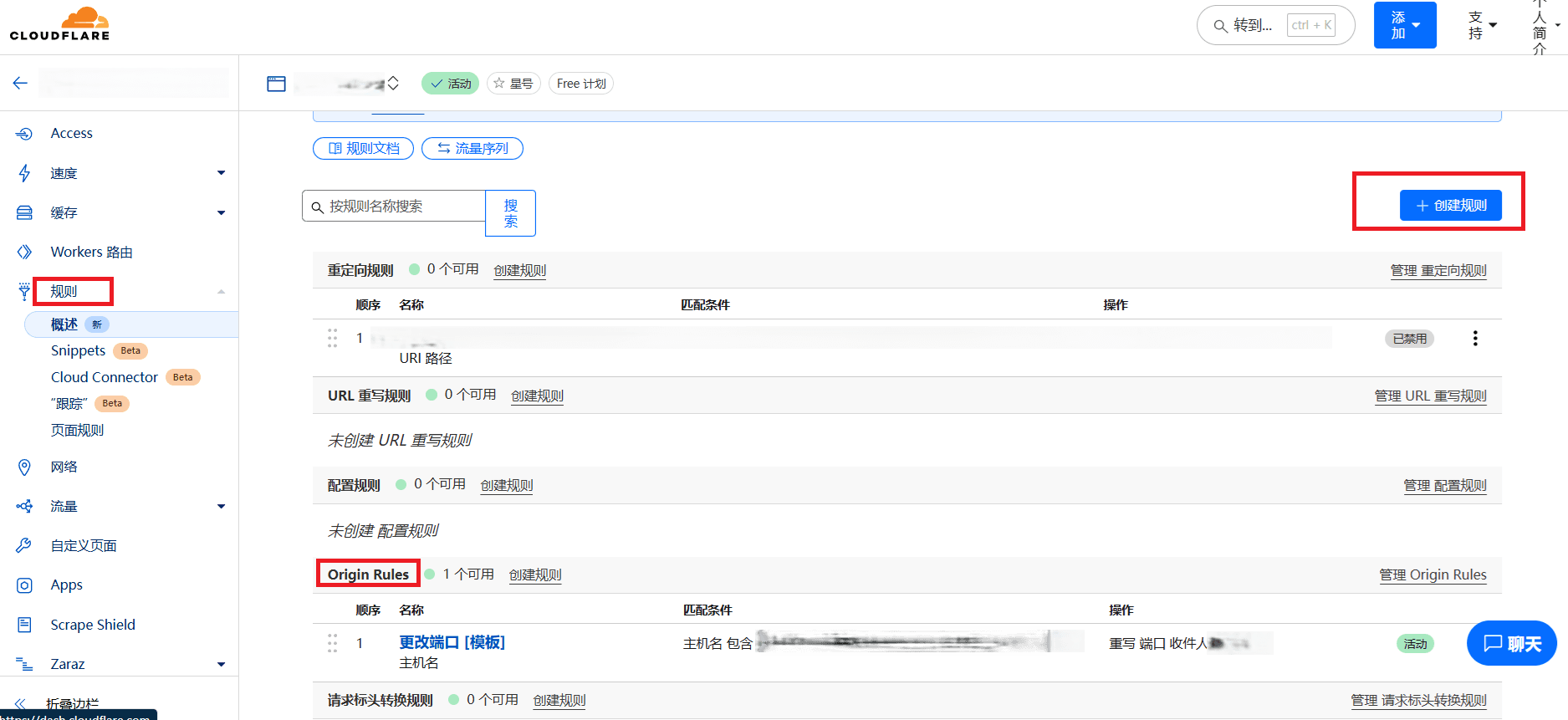 Rule - Create Rule
Rule - Create Rule
 Template - Change Port
Template - Change Port
Custom filtering expression, the first rule selects wildcard to match all subdomains, and additional rules can be added for personalized needs, such as the jellyfin service in the image not being redirected to avoid "CDN speed reduction."
Finally, enable the "little cloud" for the domains that need redirection.
- Enable Always Use HTTPS for forced redirection
- SSL certificate automation:
- Use acme to apply for Let's Encrypt wildcard certificate
- Automatic certificate renewal
- If certificate application fails, proxy configuration may be needed
3.3 Attack Surface Reduction Strategy
-
Strengthening IP whitelist: Limit source station access through CDN firewall (only allow CDN node IPs)
# Windows Firewall inbound rule (Admin PowerShell) New-NetFirewallRule -DisplayName "Allow_CDN_IPs" -Direction Inbound -LocalPort 8765 -Protocol TCP -Action Allow -RemoteAddress 173.245.48.0/20,103.21.244.0/22 -
Protocol security hardening:
- Disable TLS 1.0/1.1
Configure the minimum TLS version in Lucky to TLS 1.2 - Configure HSTS header
- Disable TLS 1.0/1.1
Add response header in reverse proxy module
add_header Strict-Transport-Security "max-age=31536000; includeSubDomains; preload";
It is recommended to understand in detail before configuring the preload option; all subdomains must comply with HTTPS, and once a non-compliant subdomain is found (including non-publicly accessible internal subdomains), the deletion process is very slow and painful.
4. Reader Interaction Section#
- Open discussion:
"If you have physical server resources, would you switch to WireGuard to establish a VPN tunnel? Why?"
5. Technical Detail Enhancement Suggestions#
- Traffic Obfuscation Techniques: Add a disguised
/health-checkpath in CDN configuration that returns a false 404 page to confuse scanners. - Responding to threats from scanners like fofa: Configure the default rule for reverse proxy to "close connection," detailed reference can be found at: Using lucky to configure reverse proxy for relatively secure WEB access on Windows - Bilibili
